The idea behind penetration testing is to identify security-related vulnerabilities in a software application. Also known as pen testing, the experts who perform this testing are called ethical hackers who detect the activities conducted by criminal or black hat hackers.
Penetration testing aims in preventing security attacks by conducting a security attack to know what damage can a hacker cause if a security breach is attempted, the outcomes of such practices help in making the applications and software more secure and potent.
So, if you use any software application for your business, a pen-testing technique will help you check the network security threats. To carry forward this activity, we bring to you this list of the best penetration testing tools!
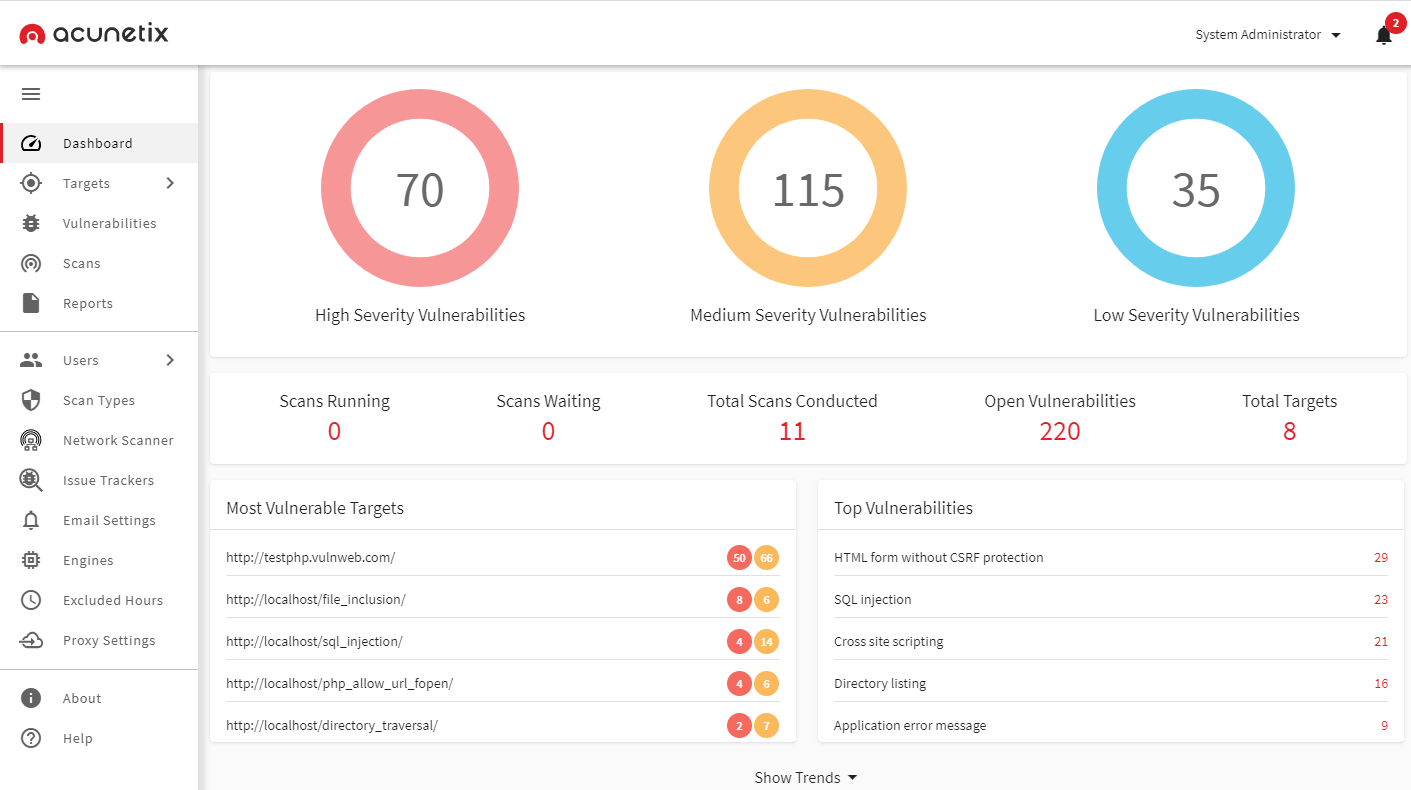
1. Acunetix
A completely automated web scanner, Acunetix checks for vulnerabilities by identifying above 4500 web-based application threats which also includes XSS and SQL injections. This tool works by automating the tasks which might take several hours if done manually to provide desirable and stable results.
This threat detection tool supports javascript, HTML5, and single-page applications including CMS systems, and acquires advanced manual tools linked with WAFs and Issue Trackers for pen testers.
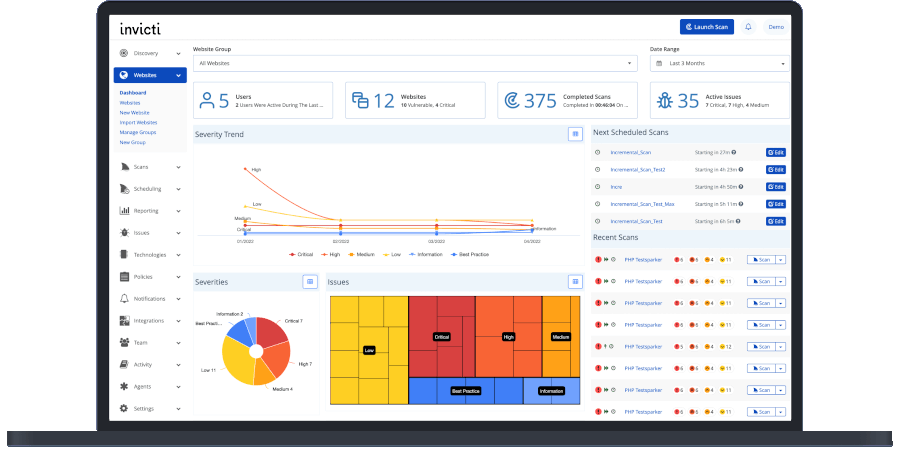
2. Invicti
Invicti is another automated scanner available for Windows and an online service that detects threats related to Cross-site Scripting and SQL Injections in web applications and APIs.
This tool checks for vulnerabilities to prove as if they are real and not false positives so that you don’t have to spend long hours checking vulnerabilities manually.
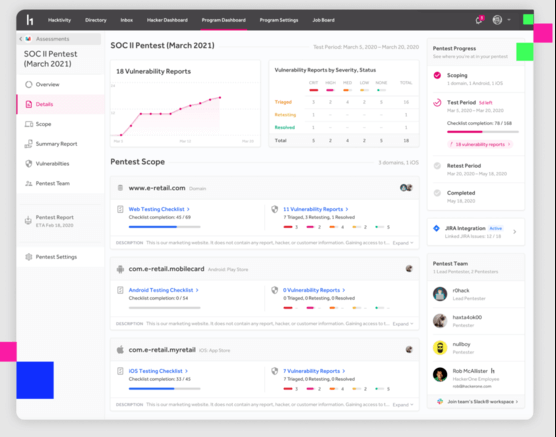
3. Hackerone
To find and fix the most sensitive threats, there is nothing that can beat this top security tool “Hackerone”. This quick and efficient tool runs on a hacker-powered platform that instantly provides a report if any threat is found.
It opens a channel to let you connect with your team directly with tools like Slack while offering interaction with Jira and GitHub to let you associate with development teams.
This tool features compliance standards such as ISO, SOC2, HITRUST, PCI, and so on without any additional re-testing cost.
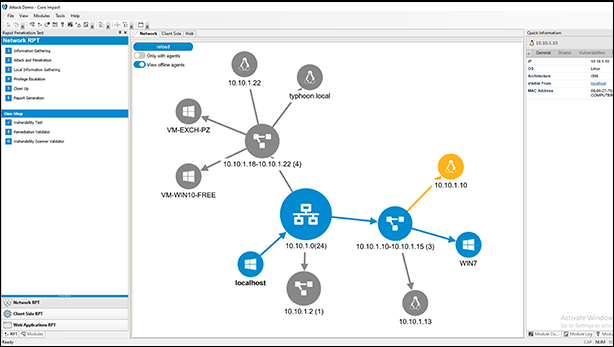
4. Core Impact
Core Impact has an impressive range of exploits in the market which allows you to execute the free Metasploit exploits within the framework.
With an ability to automate the processes with wizards, they feature an audit trail for PowerShell commands to re-test the clients by just replaying the audit.
Core Impact writes its own Commercial Grade exploits to provide top-notch quality with technical support for their platform and exploits.
5. Intruder
Intruder offers the best and the most workable way to find vulnerabilities related to cybersecurity while explaining the risks and helping out with the remedies to cut off the breach. This automated tool is for penetration testing and houses more than 9000 security checks.
The security checks of this tool feature missing patches, common web application issues like SQN Injections, and misconfigurations. This tool also aligns the outcomes on the basis of context and thoroughly scans your systems for threats.
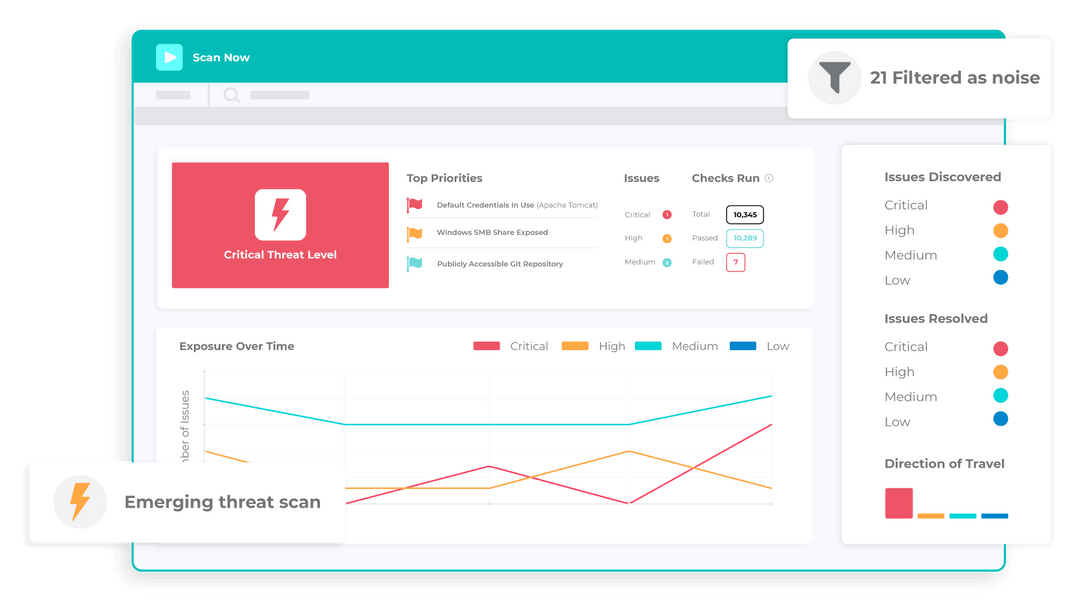
6. Breachlock
Breachlock or RATA (Reliable Attack Testing Automation) web application threat detection scanner is an AI or artificial intelligence, cloud, and human hacking-based automated scanner that needs special skills or expertise or any installation of hardware or software.
The scanner opens with a couple of clicks to check for vulnerabilities and notifies you with a report of findings with recommended solutions to overcome the problem. This tool can be integrated with JIRA, Trello, Jenkins, and Slack and provides real-time results without false positives.
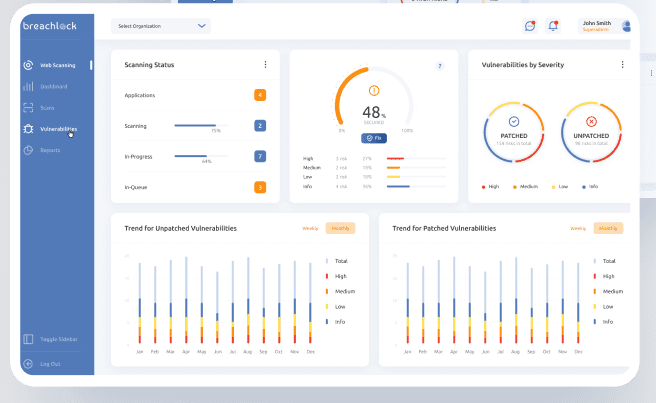
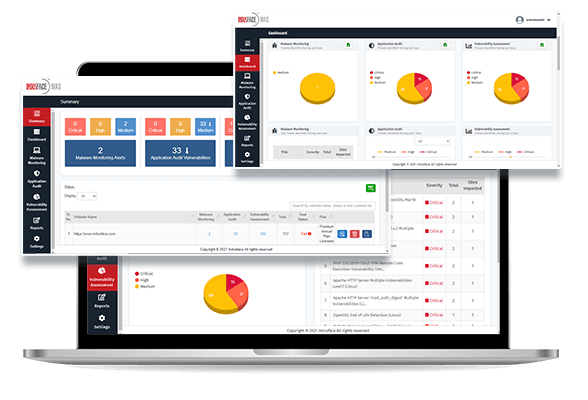
7. Indusface Was
Indusface Was is for manual penetration testing combined with its automated vulnerability scanner for detection and reporting of potential threats on the basis of OWASP vehicle including website reputation links check, malware check, and defacement check on the website.
Anyone performing manual PT will automatically receive an automated scanner that can be used on-demand for the entire year. Some of its features include:
- Pause and resume
- Scan single-page applications.
- Endless proof of concept requests to provide reported evidence.
- Scanning for malware infections, defacement, broken links, and reputation of links.
- Throughout supports for discussing POC and remediation guidelines.
- Free trial for a comprehensive single scan without any credit card details.
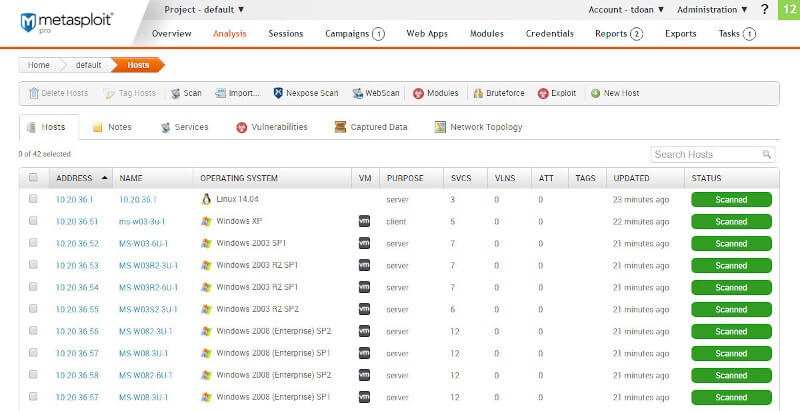
8. Metasploit
Metasploit an advanced and sought-after framework for penetration testing is based on an exploit that includes a code that can pass through the security standards to intrude into any system. On intruding, it executes a payload to conduct operations on the target machine to create an ideal framework for pen testing.
This tool can be used for networks, web applications, servers, etc. Plus, it features GUI clickable interface and command line that works with Windows, Mac, and Linux.
9. w3af
w3af web application attack and audit framework are housed with web integrations and proxy servers in codes, HTTP requests, and injecting payloads into different sorts of HTTP requests, and so on. The w3af is equipped with a command-line interface that works for Windows, Linux, and macOS.
10. Wireshark
Wireshark is a popular network protocol analyzer that provides every minor detail related to packet information, network protocol, decryption, etc.
Suitable for Windows, Solaris, NetBSD, OS X, Linux, and more, it fetches data using Wireshark which can be witnessed via TTY mode TShark utility or GUI.
11. Nessus
Nessus is one of the robust and impressive threat detection scanners that expertise in sensitive data search, compliance checks, website scanning, and so on to identify weak spots. Compatible with multi-environments, it is one of the best tools to opt for.
12. Kali Linux
Overlooked by Offensive Security, Kali Linux is an open-source Linux distribution that comes with full customization of Kali ISOs, Accessibility, Full Disk Encryption, Live USB with Multiple Persistence Stores, Android Compatibility, Disk Encryption on Raspberry Pi2, and more.
Besides, it also features some of the pen testing tools like Tools listing, version tracking, and Metapackages, etc., making it an ideal tool.
13. OWASP ZAP Zed Attack Proxy
Zap is a free pen-testing tool that scans for security vulnerabilities on web applications. It uses multiple scanners, spiders, proxy intercepting aspects, etc. to find out the possible threats. Suitable for most platforms, this tool won’t let you down.
14. Sqlmap
Sqlmap is another open-source penetration testing tool that cannot be missed. It is primarily used for identifying and exploiting SQL injection problems in applications and hacking on database servers. Sqlmap uses a command-line interface and is compatible with platforms like Apple, Linux, Mac, and Windows.
15. John The Ripper
John the Ripper is made to work in the majority of environments however, it was created mainly for Unix systems. This one of the fastest pen-testing tools comes with a password hash code and strength checking code to let you integrate it into your system or software, making it a unique option.
This tool can be availed for free or else you can also opt for its pro version for some additional features.
16. Burp Suite
Burp Suite is a cost-effective pen-testing tool that has marked a benchmark in the world of testing. This canning tool intercepts proxy, web application scanning, crawling content, and functionality, etc. it can be used with Linux, Windows, and macOS.
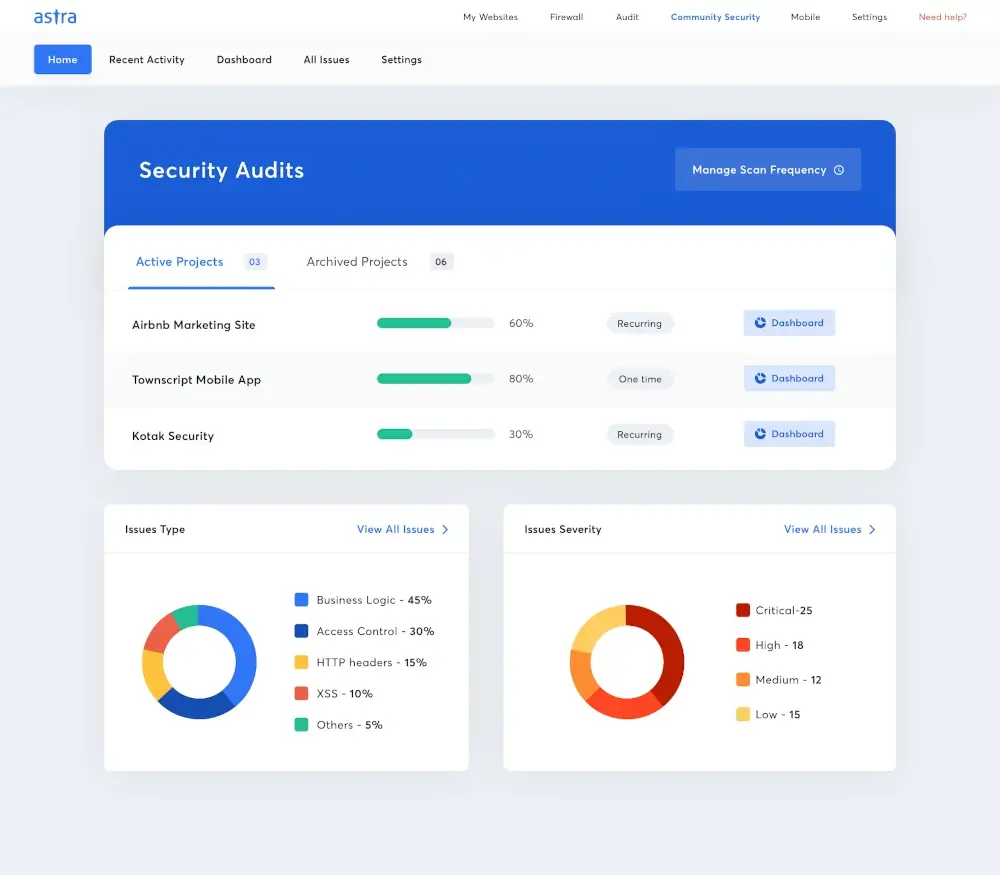
17. Astra Pentest
Astra Pentest is a service that provides both automated and manual pentesting for web, mobile, and API applications. It tests for common vulnerabilities such as OWASP Top 10 and SANS 25, as well as business logic errors and payment manipulation. It also helps you manage and prioritize your vulnerabilities, and integrates with popular tools like Jira and Slack.
Astra Pentest follows NIST and OWASP testing methodologies and helps you with compliance requirements such as SOC2, GDPR, HIPAA, PCI-DSS, and ISO 27001.
You also get a publicly verifiable Pentest Certificate after every successful pentest to boost your customer trust. It is affordable, starting from $199 per month, and offers excellent customer support from security experts. It also offers a trial package starting at $7 per week.
Conclusion
There is nothing beyond maintaining proper security while identifying tangible threats and damage that can be caused to your system by criminal hackers. But don’t you worry as, with the implementation of the above-given tools, you will be able to keep a keen eye on such activities while getting timely informed on the same to take further action?
