It is surprising how many people are interested in learning how to hack. Could it be because they usually have a Hollywood-based impression in their minds?
Anyway, thanks to the open-source community we can list out a number of hacking tools to suit every one of your needs. Just remember to keep it ethical!
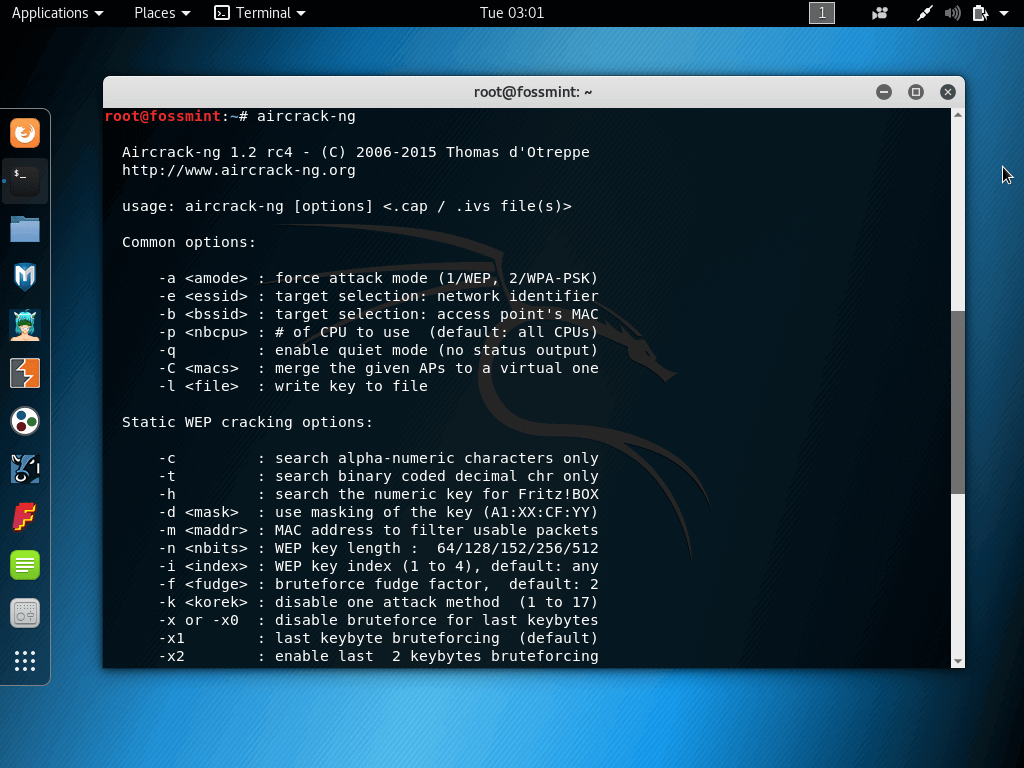
1. Aircrack-ng
Aircrack-ng is one of the best wireless password hack tools for WEP/WAP/WPA2 cracking utilized worldwide!
It works by taking packets of the network, analyses it via passwords recovered. It also possesses a console interface. In addition to this, Aircrack-ng also makes use of standard FMS (Fluhrer, Mantin, and Shamir) attack along with a few optimizations such as the KoreK attacks and PTW attack to quicken the attack which is faster than the WEP.
If you find Aircrack-ng hard to use, simply check for tutorials available online.
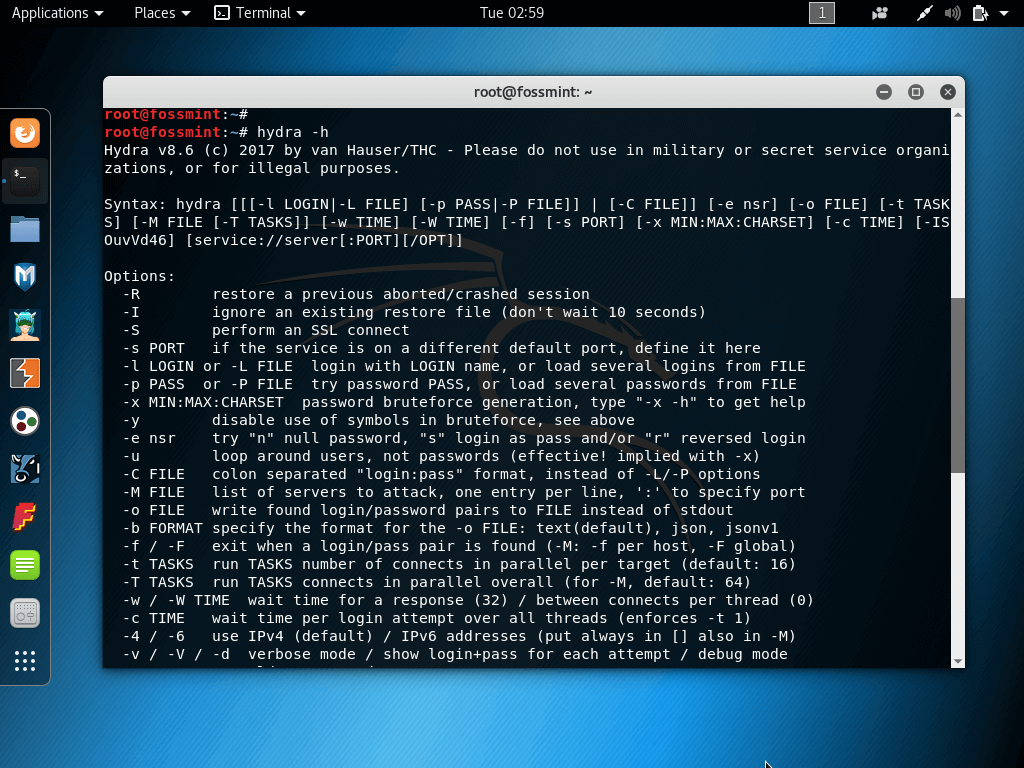
2. THC Hydra
THC Hydra uses brute force attack to crack virtually any remote authentication service. It supports rapid dictionary attacks for 50+ protocols including ftp, https, telnet, etc.
You can use it to crack into web scanners, wireless networks, packet crafters, gmail, etc.
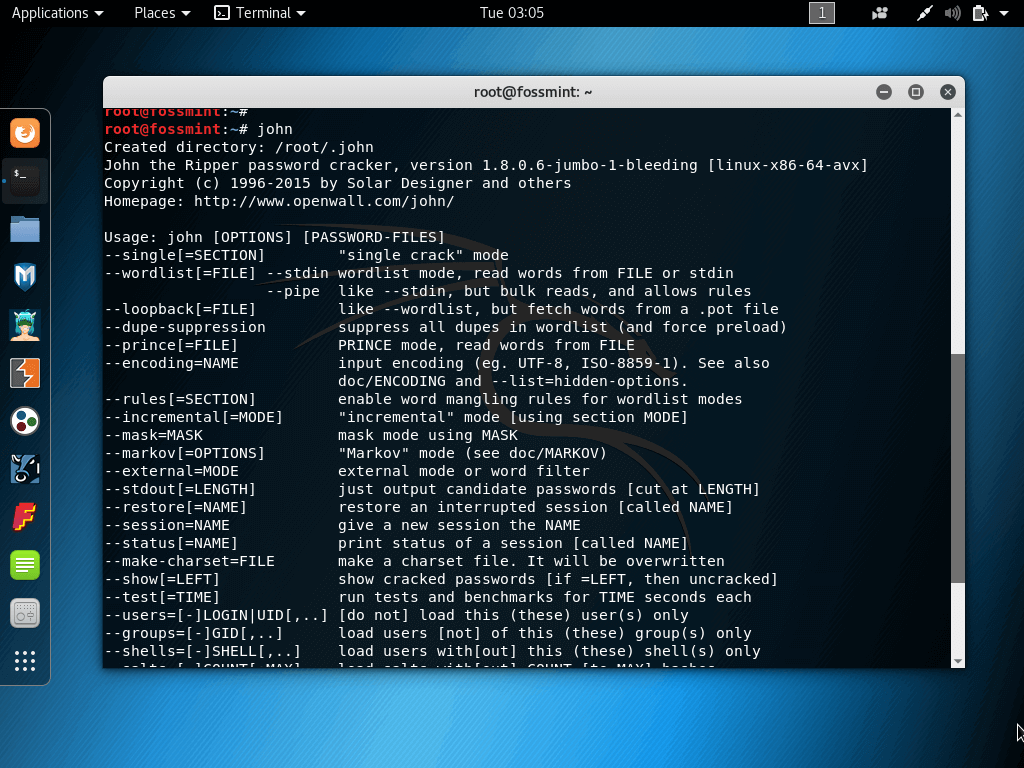
3. John the Ripper
John the Ripper is another popular cracking tool used in the penetration testing (and hacking) community. It was initially developed for Unix systems but has grown to be available on over 10 OS distros.
It features a customizable cracker, automatic password hash detection, brute force attack, and dictionary attack (among other cracking modes).
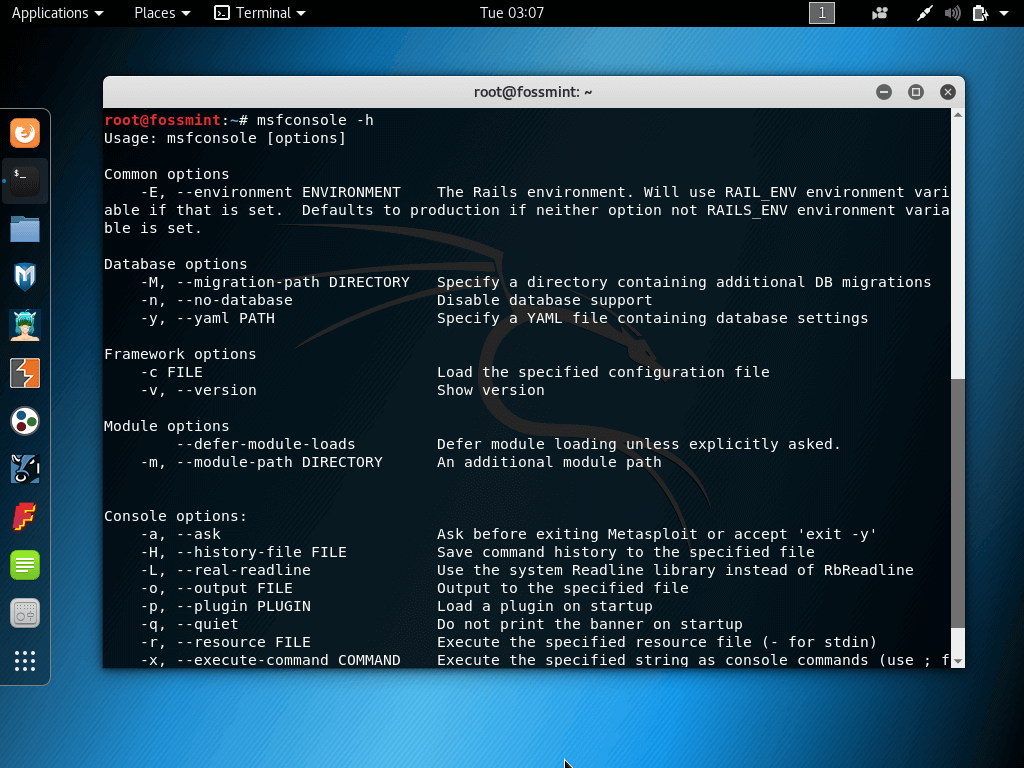
4. Metasploit Framework
Metasploit Framework is an open source framework with which security experts and teams verify vulnerabilities as well as run security assessments in order to better security awareness.
It features a plethora of tools with which you can create security environments for vulnerability testing and it works as a penetration testing system.
5. Netcat
Netcat, usually abbreviated to nc, is a network utility with which you can use TCP/IP protocols to read and write data across network connections.
You can use it to create any kind of connection as well as to explore and debug networks using tunneling mode, port-scanning, etc.
6. Nmap (“Network Mapper”)
Network Mapper is a free and open-source utility tool used by system administrators to discover networks and audit their security.
It is swift in operation, well documented, features a GUI, supports data transfer, network inventory, etc.
7. Nessus
Nessus is a remote scanning tool that you can use to check computers for security vulnerabilities. It does not actively block any vulnerabilities that your computers have but it will be able to sniff them out by quickly running 1200+ vulnerability checks and throwing alerts when any security patches need to be made.
8. WireShark
WireShark is an open-source packet analyzer that you can use free of charge. With it you can see the activities on a network from a microscopic level coupled with pcap file access, customizable reports, advanced triggers, alerts, etc.
It is reportedly the world’s most widely-used network protocol analyzer for Linux.
9. Snort
Snort is a free and open-source NIDS with which you can detect security vulnerabilities in your computer.
With it you can run traffic analysis, content searching/matching, packet logging on IP networks, and detect a variety of network attacks, among other features, all in real-time.
10. Kismet Wireless
Kismet Wireless is a intrusion detection system, network detector, and password sniffer. It works predominantly with Wi-Fi (IEEE 802.11) networks and can have its functionality extended using plugins.
11. Nikto
Nikto2 is a free and open-source web scanner for performing quick comprehensive tests against items on the web. It does this by looking out for over 6500 potentially dangerous files, outdated program versions, vulnerable server configurations, and server-specif problems.
12. Yersinia
Yersinia, named after the yersinia bacteria, is a network utility too designed to exploit vulnerable network protocols by pretending to be a secure network system analyzing and testing framework.
It features attacks for IEEE 802.1Q, Hot Standby Router Protocol (HSRP), Cisco Discovery Protocol (CDP), etc.
13. Burp Suite Scanner
Burp Suite Scanner is a professional integrated GUI platform for testing the security vulnerabilities of web applications.
It bundles all of its testing and penetration tools into a Community (free) edition, and professional ($349 /user /year) edition.

14. Hashcat
Hashcat is known in the security experts’ community among the world’s fastest and most advanced password cracker and recovery utility tool. It is open-source and features an in-kernel rule engine, 200+ Hash-types, a built-in benchmarking system, etc.
15. Maltego
Maltego is propriety software but is widely used for open-source forensics and intelligence. It is a GUI link analysis utility tool that provides real-time data mining along with illustrated information sets using node-based graphs and multiple order connections.
16. BeEF (The Browser Exploitation Framework)
BeEF, as the name implies, is a penetration tool that focuses on browser vulnerabilities. With it you can asses the security strength of a target environment using client-side attack vectors.
17. Fern Wifi Cracker
Fern Wifi Cracker is a Python-based GUI wireless security tool for auditing network vulnerabilities. With it, you can crack and recover WEP/WPA/WPS keys as well as several network-based attacks on Ethernet-based networks.
18. GNU MAC Changer
GNU MAC Changer is a network utility that facilitates an easier and quicker manipulation of network interfaces’ MAC addresses.
19. Wifite2
Wifite2 is a free and open-source Python-based wireless network auditing utility tool designed to work perfectly with pen-testing distros. It is a complete rewrite of Wifite and thus, features an improved performance.
It does a good job at decloaking and cracking hidden access points, cracking weak WEP passwords using a list of cracking techniques, etc.
20 .Pixiewps
Pixiewps is a C-based brute-force offline utility tool for exploiting software implementations with little to no entropy. It was developed by Dominique Bongard in 2004 to use the “pixie-dust attack” with the intention to educate students.
Depending on the strength of the passwords you’re trying to crack, Pixiewps can get the job done in a mater of seconds or minutes.
Well, ladies and gentlemen, we’ve come to the end of our long list of Penetration testing and Hacking tools for Kali Linux.
All the listed apps are modern and are still being used today. If we missed any titles don’t hesitate to let us know in the comments section below.

thanks…
Excellent tools for hacking and penetration in Kali Linux. I will try them all..
You forgot emagnet.
Nice share
I need a tool to integrate at https://www.nmmapper.com
Nice article .
You seem to be a pro in this kali liinux tools ,
Can i ask u a question, can you recover a disabled instagram account using one of kali tools ? and if yes then what tool?
Quite a list, I always look for tools to host at Nmmapper Hosted security tools and there is a variety. So I will pick one listed above and add them there.
good article
I see that you are an expert Martins. I can not comprehend all those codes really confusing for me :(. I have read this forum about hacking – https://www.cocospy.com/blog/facebook-messenger-hack.html which might have been easier but I doubt I will be able to purchase it because it asksfor a fee. I have interest in hacking back in middle school, but never pursue the subject until now.
Great sharing bro
Thanks
There are only a handful of real hackers in the world. I have known one since we were in middle school he was always a genius with stuff like that. Now he is some sort of deep web Guru. Get him at [email protected] need his services. I can’t publicly tell you stuff that he’s done for me but bottom line is I have used him more than once and he won’t take your money without showing you some sort of proof.
Nice List! THX!
Awesome article. I am afraid the interest in hacking (especially WiFi networks) is somewhat obvious. It was much easier to ‘use’ WiFi a few years back and, if you are determined, still kind of is. These days, I find there are plenty of free WiFi access points that are perfectly legal and only require some security savvy.
Penalties for illegal WiFi tapping are getting to be enough to keep me on the up and up. Plus, it is too easy to be sniffed out if you are engaging in such practices.
I know when someone is sniffing on my network and if they manage to connect, I know where they are, at least, most of the time. Even if I really don’t they get a pop-up that makes them think I do. Plus, WiFi security has improved greatly. I am still perplexed by how many still don’t use it. (Windows users)
On the other side is the hacking done for other reasons. I saw an article about bounties being paid for various things such as finding vulnerabilities in browsers or exploits in software. The bounties were nothing to scoff at and got me interested in hacking, too! It wouls seem a good hacker is a sought after commodity and the pay is significant.
Of course, Hollywood makes hacking look so cool and glamorous. Who wouldn’t want all the perks the guy gets in the movie ‘Swordfish’? I know that is as far from reality as you can get but some people believe.
Thanks again for the article. You always seem to find good subjects to write about. Keep it up.